The internet is a scary place. You do everything in your power to prevent a security breach and protect yourself. You never go to seedy sites, you have the best antivirus, you never download disreputable software, you stay away from the dark web, etc.
But can we add another layer of security? Of course we can!
Domain Name System
We can leverage the DNS system to secure our machine with this technique I am about to show you. Every website, service, or device on the internet is assigned a unique address. When you enter a domain in your browser, usually your computer does not know what this address to the server is on the internet. In order to locate by domain name, your machine utilizes a DNS service to correlate the domain name, i.e. facebook.com, to its unique address, 157.240.18.35.
Once it has the Internet Protocol address, it can reach out to the web server and fetch the website or resource. Traditionally, these DNS servers are either provided by your ISP automatically when you initially connect to the internet or you can configure your machine to reach out to publicly available DNS servers on the internet.
The Host File
How can we use this system to block certain sites before our computer even has a chance to reach out to a DNS server to fetch an unsavory site or resource? Easy! The host file.
Every operating system has one, Windows, Mac, and Linux.
Your machine will always check the host file before it queries a non-local DNS server.
So what addresses do I block?
Luckily for us, Steven Black has done all the hard work curating large lists of DNS blacklists and maintains them on a Github repository. His repository provides highly specific lists to fit your needs.
https://github.com/StevenBlack/hosts
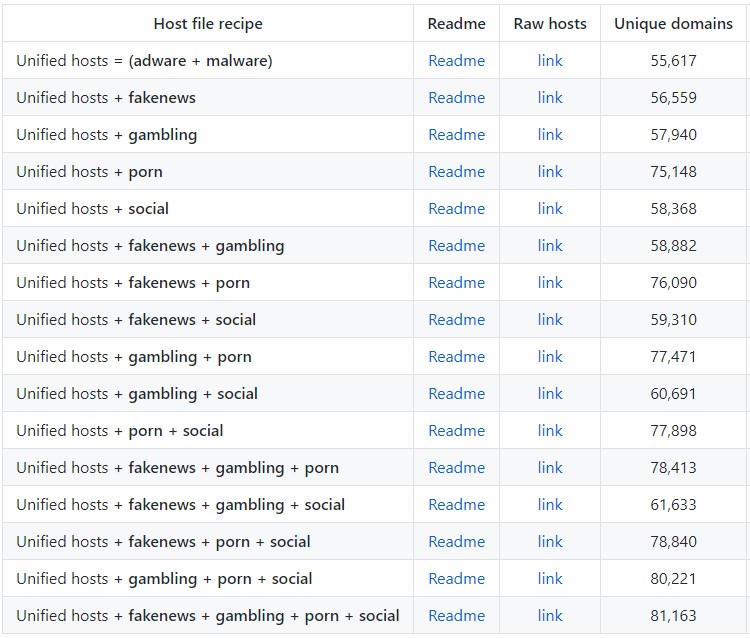
As you can see, you can select from a wide variety of categories; adware, malware, fake news, gambling, p*rn, and social media. These host files work like this…
Let’s say we accidentally go to yourfreep*rn.us? Oops!
Well, let’s look into one of the curated host files.
0.0.0.0 yourfreep*rn.usAs you can see, the file associates this site with internet protocol address, 0.0.0.0. This is called a non-routable address. So instead of going out to the internet to either fetch the site or to a DNS server to query for location, it essentially doesn’t nothing. Your request goes into a void and the result is your browser complains that the site can’t be reached. Perfect!
Great but where is the host files located?
As I said before, all operating systems have a host file.
Windows host file location
%SystemRoot%\System32\drivers\etc\hostsLinux and Mac host file location
/etc/hosts
# or
/private/etc/hostsNow all you have to do is open up this file with either Notepad or the terminal, copy/paste in the specific list you selected from the git repository and save the file. Note: Notepad or terminal must be opened in elevated administrator mode due the host file being a system file to be modified.
That’s it! That is all you have to do to add another layer of security to your defenses. This can save you from a phishing attack, block disreputable adware, keep your children away from p*rn at an early age, and even block social media entirely that takes entirely too much of your time!
Much thanks to Steven Black that keeps these curated host files updated nearly everyday.
Comments are closed, but trackbacks and pingbacks are open.